Introduction
Definition: User
A user in Linux is an abstraction for keeping track of three things:
- permissions - what can be done and by whom;
- accountability - who is doing what;
- ownership - who owns what.
We can logically divide users into three types:
- The Superuser
rootis the most powerful user and is present on every Linux system. It is allowed to do pretty much anything. - Regular users usually correspond to real people. For example, there could be a user
bobfor your colleague Bob or a useralicefor your manager Alice. - System users are low-privileged users which are created for performing very specific tasks. For example, there could be a
dbuser for managing databases. This “division of labor” enhances security.
Users can start processes, and own files and directories. Furthermore, users can be added to groups to share permissions.
Representation
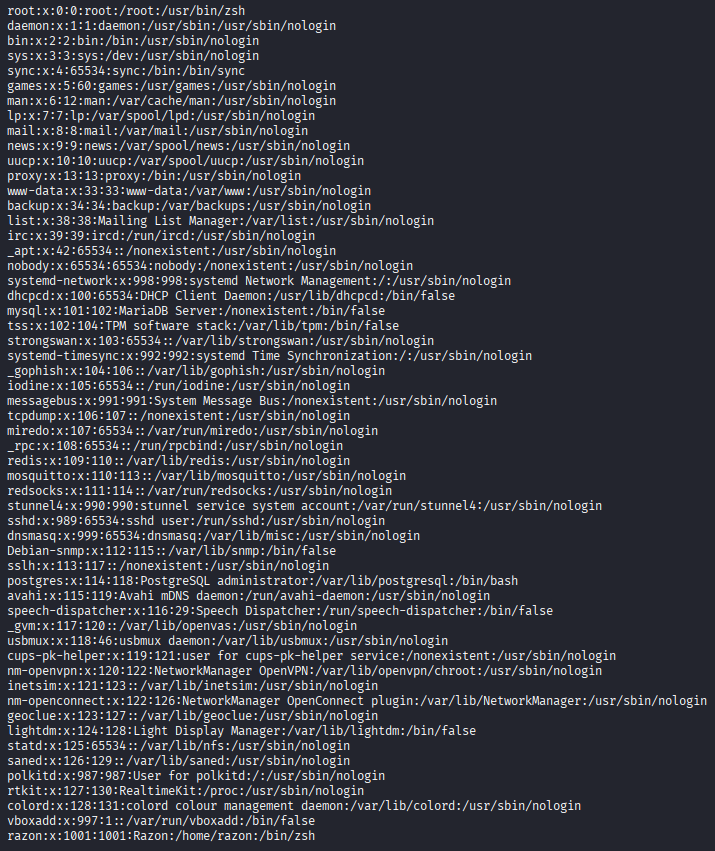
User information is stored in the plain-text /etc/passwd file. Each line represents one user and has the following format:
username:password:UID:GID:GECOS:home:shell
- The
usernamefield contains the user’s name. It is unique for every user. - The
passwordfield used to contain the hash of the user’s password. Nowadays, it contains either an asterisk (*) or the letterx, while the hash itself is stored in the/etc/shadowfile. This is because the/etc/passwdfile is meant to be readable by anyone and exposing password hashes is never a good idea. The/etc/shadowfile, on the other hand, is only readable by the superuserroot. - The
UID(user ID) field is a non-negative integer which is unique to each user. The UID 0 is reserved for the superuserrootand UIDs in the range 1-999 are reserved for system users. This means that the UIDs of regular users usually begin at 1000 and onwards. - Every user must belong to at least one group, known as their primary group, and the ID of this group is stored in the
GID(primary group ID) field. - The
GECOSfield is often called the comment field and serves a purely informational purpose. It is usually used for the full name of the person behind the user, but can contain pretty much anything else, too. - A user can have a default directory assigned to them where they can store their files. This is known as their home directory and the
homefield contains the absolute path to it. Thehomefield is also used to set theHOMEenviroment variable. - A user can also have a default shell assigned to them which is used when they log in. The
shellfield contains the absolute path to this shell and is also used to set the value of theSHELLenvironment variable. System users usually do not have a default shell and theirshellfield is either empty or the ends innologinorfalse.
Example: Typical
/etc/passwdFileA typical
/etc/passwdlooks like this:
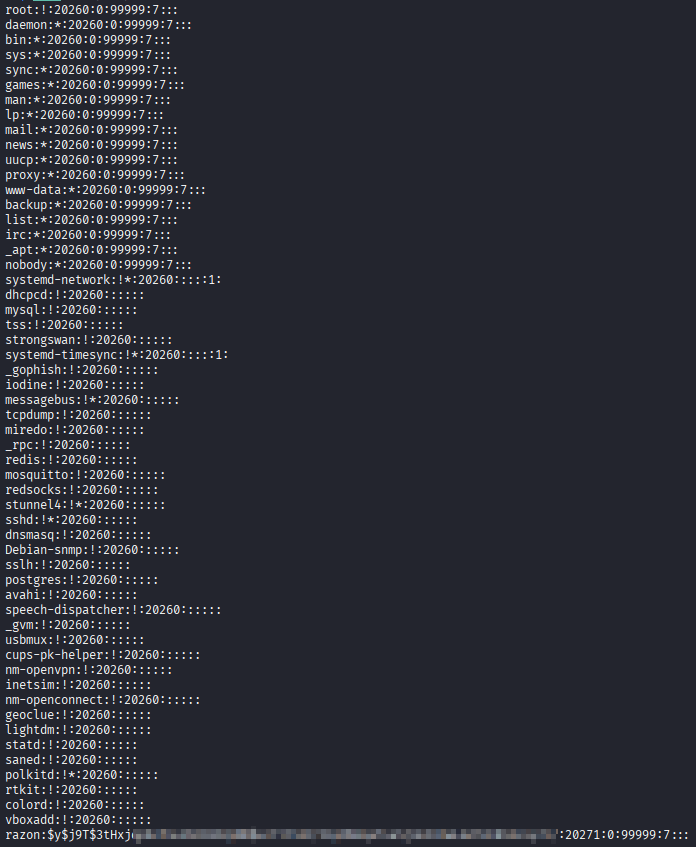
Furthermore, each user also has a corresponding line in the /etc/shadow file. This file should only be readable by the superuser root because it contains sensitive information such as the hash of the password of each user. Every line has the following format:
username:hash:last_changed:min_password_age:max_password_age:password_warning_period:password_inactivity_period:account_expiration_date:reserved
- The
usernamefield contains the user’s name. - The
hashfield contains the hash of the user’s password. If empty, then the user has no password. Note that many applications refuse to operate if the user has no password. If this field contains*or!, then password login is disabled for this user. - The
last_changedfield contains the date of the last time the password was changed. It is expressed as the number of days since Jan 1, 1970 00:00 UTC. A value of 0 means that the user should change their password the next time they log in. If this field is empty, then password aging features are disabled. - The
min_password_agefield stores the number of days the user has to wait after a password change before they can change their password again. A value of 0 indicates that the user does not have to wait at all. - The
max_password_agefield is the number of days is the number of days since the last password change after which the password will expire and the user will be asked to change their password again. An empty field indicates that there is no such period, no password warning period and no password inactivity period. Ifmax_password_ageis lower thanmin_password_age, then the user is unable to change their password. - The
password_warning_periodis the number of days before the password expires during which the user will be warned that their password will soon expire. An empty field and a value of 0 indicate a lack of such a period. - The
password_inactivity_periodis the number of days after the password expires during which it should still be accepted. Once the password has expired and this period has passed, the user can no longer log in with their password. An empty field means that such a period is not enforced and is essentially indefinite. - The
account_expiration_dateis the date of expiration of the user. It is expressed in number of days since Jan 1, 1970 00:00 UTC. After this date, the user cannot login at all. A value of 0 can be interpreted either as an account with no expiration or as an account with an expiration date of Jan 1, 1970. - The
reservedfield is reserved for future use.
Example: Typical
/etc/shadowFileA typical
/etc/shadowfile looks like this: